
A jail telephone must deliver secure and reliable communication in correctional settings. Facilities often choose a visitation prison telephone with tamper-resistant features. The wall mounted prison telephone design helps prevent unauthorized access. Many institutions trust a vandal proof prison telephone to withstand harsh environments and deter misuse.
Jail Telephone Security Threats
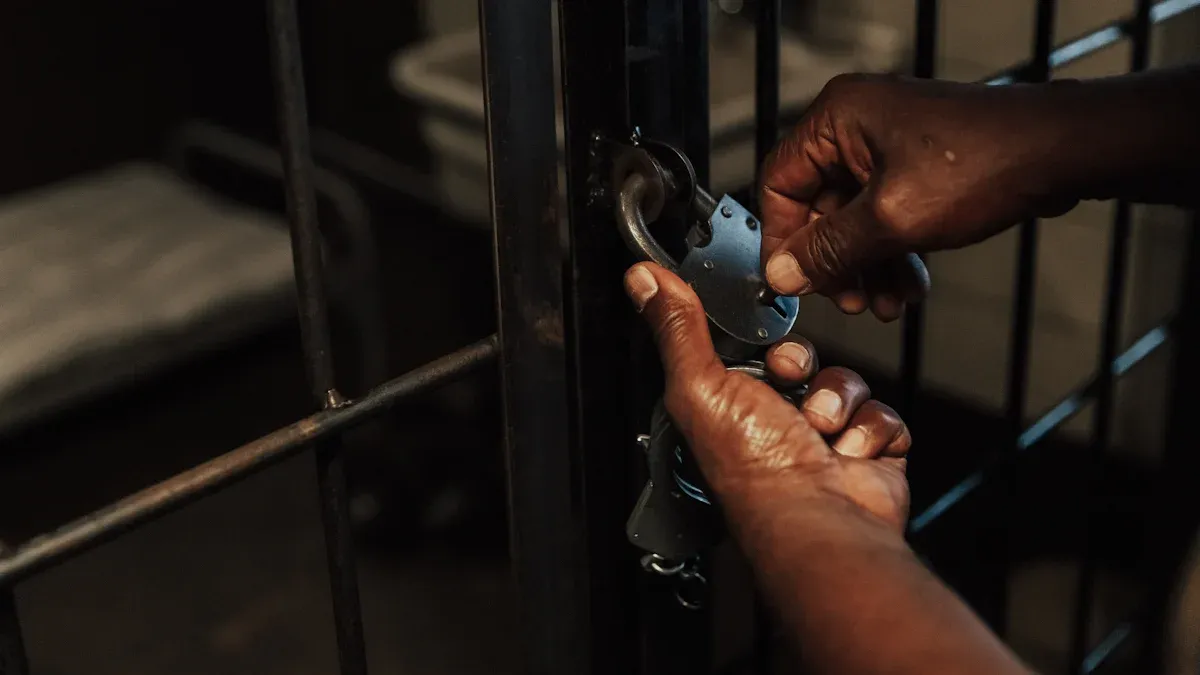
Tampering and Physical Interference
Correctional facilities face constant risks from tampering and physical interference with jail telephone systems. Inmates may attempt to damage or disable telephones to disrupt communication or avoid monitoring. Some try to remove parts or use makeshift tools to access internal components. These actions can lead to costly repairs and compromise security. Facilities rely on vandal-resistant designs to prevent such incidents and maintain reliable communication.
Impersonation and Unauthorized Use
Impersonation and unauthorized use present serious challenges in correctional environments. Inmates sometimes use another person’s identification or credentials to access a jail telephone. This misuse allows them to make calls without detection or accountability. Reports show that telephone abuse is widespread. Inmates have used jail telephones to commit crimes such as fraud, witness intimidation, and drug conspiracies. Law enforcement agencies have documented cases where inmates arranged murders or conducted financial scams using these systems.
Contraband and Illicit Communications
Contraband cell phones pose a major threat in correctional facilities. Inmates smuggle wireless devices using creative concealment methods, including body cavities and false containers. Some receive help from visitors or corrupt staff. With these phones, inmates can coordinate escapes, threaten witnesses, and bypass monitoring systems. The Federal Communications Commission considers a cell phone in an inmate’s possession as dangerous as a weapon. Thousands of devices have been confiscated in single facility searches. Detection efforts include random inspections, metal detectors, and specially trained dogs. Despite these measures, large volumes of inmate communications remain unanalyzed, making it difficult to detect all illicit activities.
Jail Telephone Security Features and Technologies

Tamper-Resistant Hardware and Vandal-Proof Design
Correctional facilities require phones that can withstand harsh environments and frequent abuse. Manufacturers design jail telephones with tamper-resistant hardware and vandal-proof features to address these needs.
- Reinforced stainless steel casings provide strong impact resistance and prevent corrosion.
- Security screws and armored handset cords stop unauthorized disassembly and reduce the risk of tampering.
- Pry-proof buttons and tamper-proof wiring systems add extra layers of protection.
- Wall-mounted designs with cable entrances at the back make it difficult for inmates to damage or access internal components.
- Phones like the Joiwo Vandal Proof Visitation Telephone JWAT146 meet the IK10 anti-vandalism standard and hold certifications such as FCC, CE, RoHS, and ISO9001, confirming their reliability in demanding settings.
These features ensure the jail telephone remains operational and secure, even under extreme conditions.
Encrypted Communications and Secure Connections
Modern jail telephones use encryption to protect sensitive conversations. Encryption technology converts call data into secure codes. Only authorized parties with the correct decryption key can access the information.
Encryption secures both calls in progress and stored data, making unauthorized access very difficult.
Facilities rely on encrypted networks and secure protocols like TLS to safeguard communications. Even if someone intercepts a call, they cannot understand the content without the decryption key. This approach prevents eavesdropping and protects the privacy of inmates and staff. Hybrid systems combine the durability of analog phones with the advanced security features of VoIP, offering both reliability and strong data protection.
Biometric and PIN Authentication
Correctional facilities use biometric authentication to verify user identities and prevent impersonation. Fingerprint recognition is the most common method.
- Fingerprint scanners at entry points and processing stations allow rapid and accurate identification.
- The system matches unique fingerprint patterns against stored templates, usually in less than a second.
- Biometric authentication supports booking, release, inmate movement tracking, and facility counts.
PIN authentication also adds a layer of security. Unlike ID cards or passwords, fingerprints cannot be lost or shared. This reduces the risk of identity fraud and unauthorized use of the jail telephone. Facilities that use biometric systems report improved security and streamlined operations.
Real-Time Monitoring and Alerts
Real-time monitoring plays a vital role in jail telephone security.
- Staff can listen to calls and record conversations to detect misuse or illegal activities.
- Systems use keyword detection and call flagging to identify suspicious behavior.
- Intrusion detection systems alert staff to unauthorized access attempts.
These technologies help facilities respond quickly to threats and maintain control over communications. Integration with emergency and paging systems enhances operational control and safety.
Real-time monitoring and access controls ensure that only authorized users can operate the jail telephone, reducing the risk of misuse.
Operational Best Practices and Real-World Results

Staff Training and Policy Enforcement
Correctional facilities rely on strong staff training and clear policy enforcement to prevent telephone misuse. Staff members who monitor calls need ongoing training, not just initial instruction. Many institutions have found that limited training for telephone monitors and insufficient staffing reduce the effectiveness of monitoring. Policy enforcement also plays a key role. When facilities increase disciplinary sanctions for telephone abuse, they send a clear message that misuse will not be tolerated. However, technology alone cannot solve these problems. Staff must understand how to use monitoring tools and follow established procedures to ensure security.
Regular System Audits and Maintenance
Routine audits and maintenance keep communication systems reliable and secure. Facilities that perform regular updates ensure all components work together and meet current standards. Centralized security systems help staff comply with regulations and make audits easier. Ongoing updates and security patches protect against new threats. These practices, common in integrated security systems, also apply to jail telephones. Consistent maintenance and audits help prevent system failures and reduce the risk of tampering.
Case Studies: Reduced Incidents and Improved Safety
Many correctional facilities have seen positive results after improving their telephone security measures. Managed telephony systems give inmates a secure way to communicate, which lowers the demand for illegal mobile phones. When facilities combine managed telephony with advanced detection and selective blocking of unauthorized devices, safety improves. Data analytics from these systems help staff manage prisons more effectively. Secure communication supports peace, rehabilitation, and social reintegration, which can reduce crime and violence inside institutions.
Reliable jail telephone systems, such as the Joiwo Vandal Proof Visitation Telephone JWAT146, deter tampering and misuse through features like stainless steel construction, tamper-resistant screws, and IK10 anti-vandalism ratings.
- Advanced call monitoring, screening, and integration with security software create safer correctional environments.
- Facilities must stay vigilant and upgrade systems to counter evolving threats from new technologies and inmate tactics.
FAQ
How does the Joiwo JWAT146 prevent tampering?
The JWAT146 uses stainless steel, tamper-resistant screws, and a vandal-proof design. These features stop unauthorized access and protect internal components.
Can inmates use the jail telephone for unauthorized calls?
Staff monitor calls and use authentication methods. The system restricts access, so only approved users can make calls.
What certifications does the Joiwo JWAT146 hold?
- CE
- FCC
- Rohs
- ISO9001
These certifications confirm safety, quality, and reliability for correctional environments.


